Security Certifications, Reports and Attestations
Learn about our commitment to information security and compliance.
Granica maintains the highest level of data security by incorporating industry leading best practices into our information security program. We are dedicated to obtaining and maintaining industry recognized security and privacy third party certifications, and to working with independent, CBA-registered CPA firms to regularly audit our program and attest to our certifications.
Benefits for our customers:
- Increased visibility and confidence in our information security program and overall operations
- Increased ease in onboarding Granica as a vendor
Benefits for Granica:
- Ensures we continue to align with industry best practices to meet the requirements of a strong and comprehensive information security program
- Streamlines the process of sharing information on our security program with potential and existing customers
Current

SOC 2 Type 1 Report: The SOC 2 report focuses on a business’s non-financial reporting controls as they relate to security, availability, processing integrity, confidentiality, and privacy of a system, as opposed to SOC 1/SSAE 16 which is focused on the financial reporting controls. The SOC 2 Type 1 (or Type I) report evaluates the effectiveness of the deployed controls at a point in time.
SOC 2 Type 2 Report: The Type 2 (or Type II) report evaluates the effectiveness of deployed controls over a period of time. This report provides greater assurance and is more comprehensive than the Type 1 report.
Planned (Roadmap)
Year(s): 2024
- ISO/IEC 27001 Report: An international standard that evaluates the effectiveness of an information security management system (ISMS). ISO/IEC 27001 addresses people and processes as well as technology.
Requesting a copy of the Granica SOC 2 Type 1 and Type 2 Reports
SOC 2 Reports are restricted and can not be shared publicly. Not only do these reports contain very detailed information about how our systems operate (which could make a potential attack against Granica easier) but these reports also contain proprietary information about how these audit firms conduct their testing. For these reasons we can only share SOC 2 reports upon request with prospective customers that are under an NDA with Granica or with current customers bound by the confidentiality of our customer agreements. The report should not be shared with anyone other than the individual requestor(s), and no parts of the report nor the entire document may be shared or disclosed to parties not covered by those agreements.
To request our SOC 2 report contact our security team via email and provide the following information:
- Company Name: {Company Name}
- Report Requestor: {First Name Last Name}
- Report Requestor email (if different from sender’s email address): {requestor.email@company.com}
- Report Requestor Job Title: {Information Security Analyst, CISO, etc.}
You will receive an acknowledgement email within one business day.
System and Organizational Controls (SOC) Overview
The American Institute of CPAs (AICPA) has developed a suite of System and Organizational Controls (SOC) reports that a Certified Public Accountant (CPA) may provide in connection with system-level controls of a service organization or entity-level controls of other organizations.
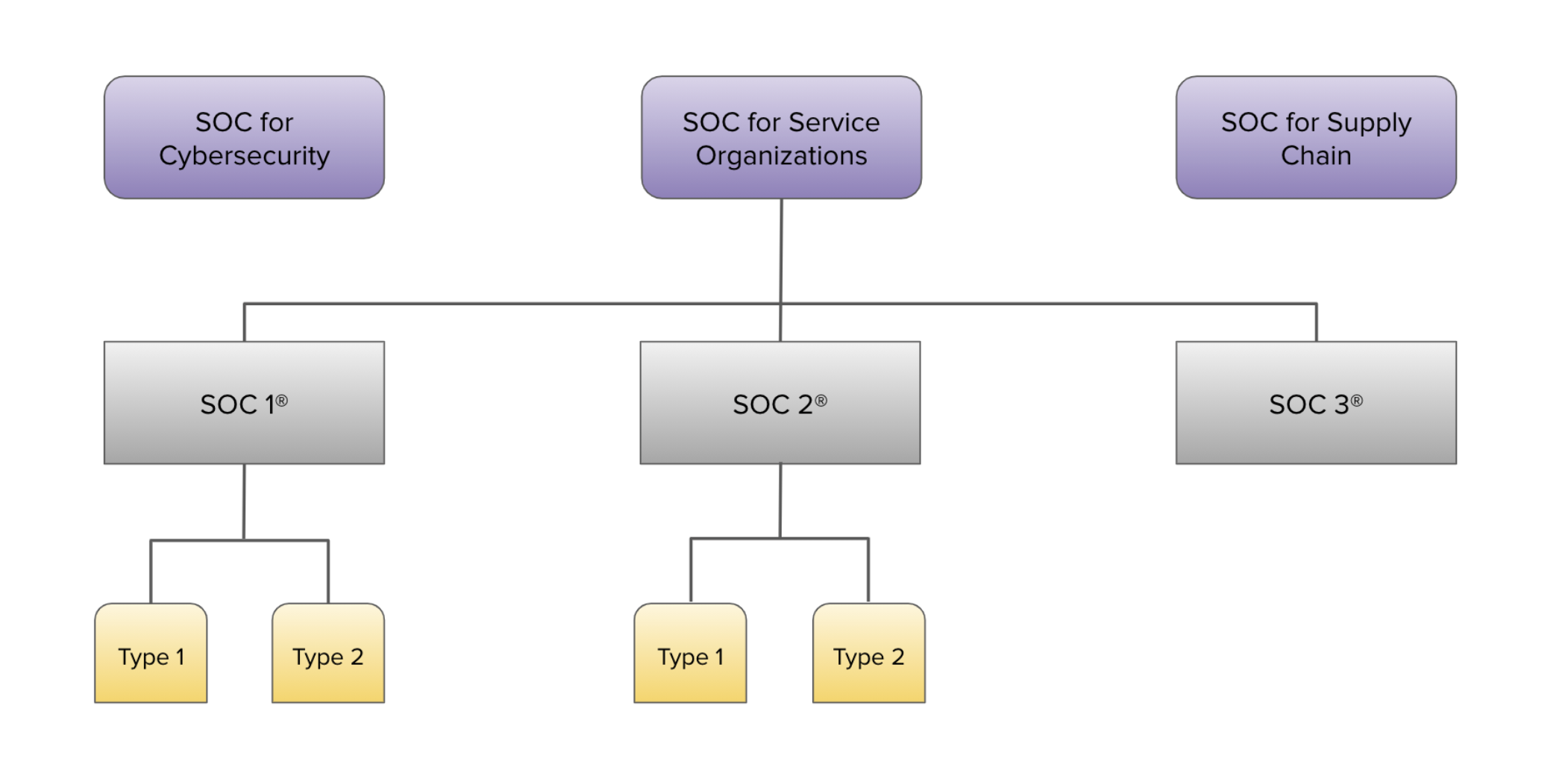
The reports offered are divided into three categories:
- SOC for Service Organizations
- SOC for Cybersecurity
- SOC for Supply Chain
Additionally, the SOC for Service Organizations category is classified into:
- SOC 1® for Service Organizations: Internal Controls over Financial Reporting (ICFR)
- SOC 2® for Service Organizations: Trust Services Criteria
- SOC 3® for Service Organizations: Trust Service for General Use Report
Type 1 and Type 2 reports are available for SOC 1 and SOC 2.
SOC 1 for Service Organizations: Internal Controls over Financial Reporting (ICFR)
The SOC 1 report is applicable when the service organization can impact its customers’ internal control over financial reporting (ICFR) such as payroll, credit card payments.
SOC 2 for Service Organizations: Trust Services Criteria
According to AICPA the SOC 2 Report covers controls at a Service Organization relevant to the following Trust Services Criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy The report must contain Security (or Common Criteria) , with the remaining Trust Services Criteria included, if applicable.
SOC 2 Type 1 Report
The Type 1 (or Type I) report evaluates the effectiveness of the deployed controls to meet the Trust Services Criteria at a point in time.
SOC 2 Type 2 Report
The Type 2 (or Type II) report evaluates the effectiveness of deployed controls to meet the Trust Services Criteria over a period of time. This report provides greater assurance and is more comprehensive than the Type 1 report.
Health Insurance Portability and Accountability Act (HIPPA)
If a customer's cloud environment is HIPAA compliant, and that customer implements proper controls around data handling, access, and separation, then using Granica can be part of an overall HIPPA compliant architecture. This is because Granica does not directly handle protected health information (PHI) or other customer data:
- Data stays within the customer's own HIPAA-compliant cloud environment (AWS, GCP etc.) and Granica does not have access to actual data contents.
- Granica relies on the cloud provider's native encryption for data at rest and in transit.
- The Granica control plane runs within the customer's VPC and follows their security policies.
- Data isolation happens automatically if the customer uses separate buckets per tenant.